Obsolete SSH servers
The SSH protocol, like any other, progresses, the hashing and encryption mechanisms are updated according to new vulnerabilities or inherent weaknesses that end up being exploitable.
This is why certain connections warn that the clients cannot negotiate the protocols proposed by the servers. All these discrepancies can be resolved for the instant connection we want to make, or we can make them persistent. In this example, the machine 192.168.1.201, when we try to connect to it, fails because the client can no longer negotiate the DSA public key algorithm:
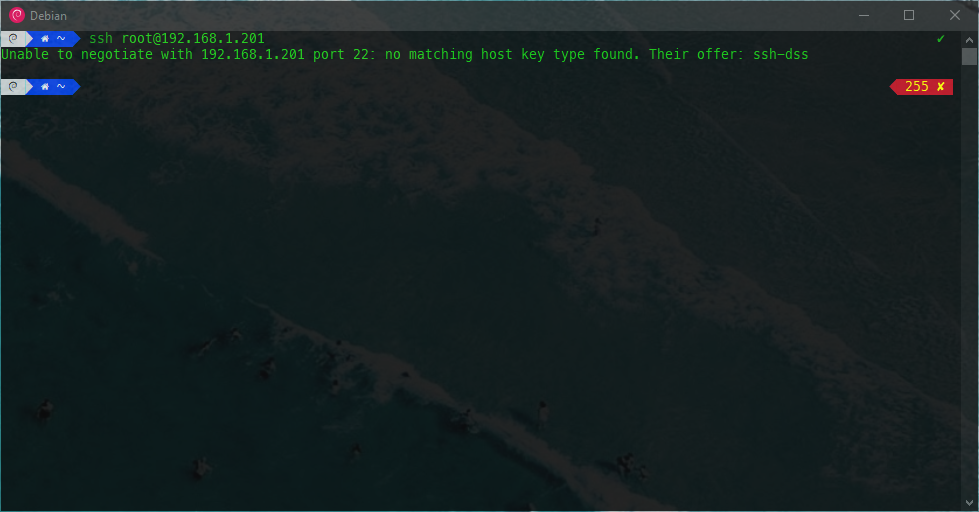
Specifically this happens since version 7.0 of OpenSSH , and it is not a bad thing, it simply indicates that ssh-dss is deprecated, and although it is offered by the server, we should not use it.
As it is not always feasible to update the server (OT environments, non-upgradable machines, old firmware, etc…), it is very likely that we still have to connect remotely, and SSH, although with obsolete algorithms, at least does not move over the network in plain text.
Therefore, if we would like to complete this connection, we should include it at startup:
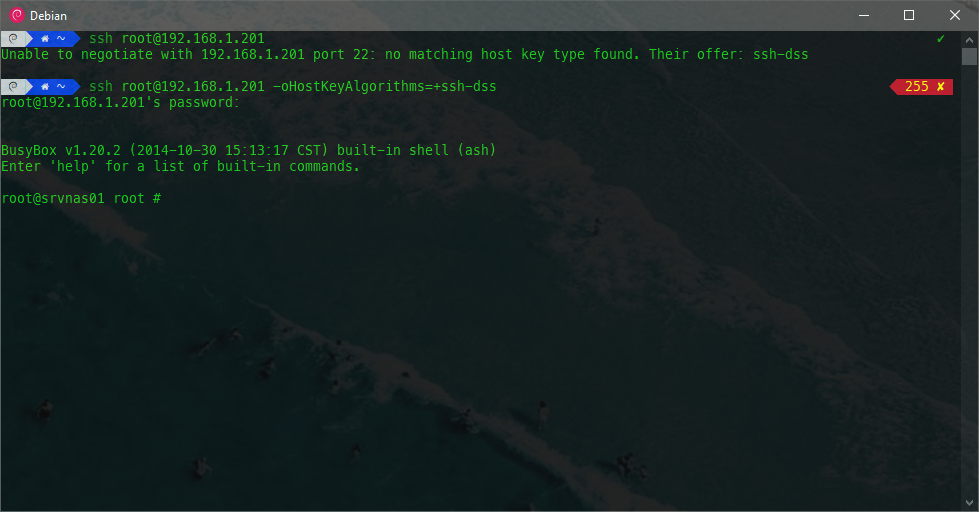
This new parameter will be needed every time we connect to the machine, unless we add DSA persistently to the list of allowed algorithms, or that must be used when connecting to certain machines. In this case, we will make it persistent only for 192.168.1.201:
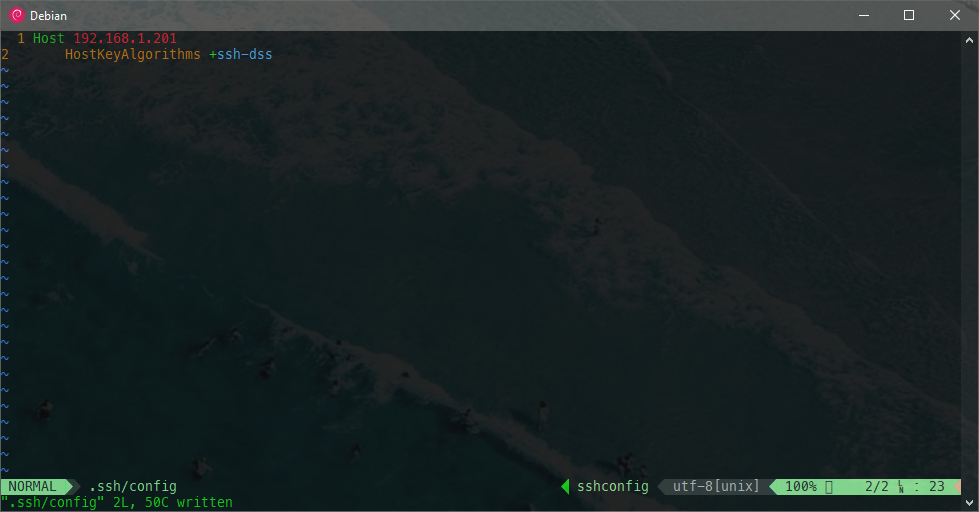
By editing the ~/.ssh/config file, we can activate or deactivate the options we consider appropriate, independently for each host.
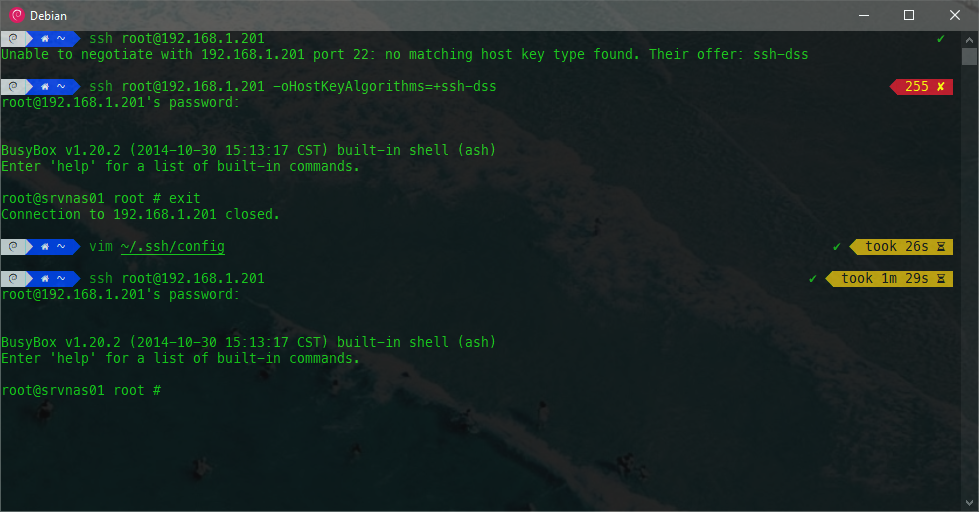
And we won’t need to remember every single case.
A very useful modifier that we have available is -G , which allows us to consult in detail all the parameters offered by the server to which we want to connect:
