Secure SSH with MFA
One of the ways to improve the security of a system and that has gained a lot of strength are the mechanisms MFA , Multi Factor Authentication. They consist in the fact that it is not only necessary to correctly enter our username and password, but it is also necessary to validate the login in an additional way. The OTP , One Time Password , codes are well known, and providers such as Google and Microsoft offer applications such as Google Authenticator and Microsoft Authenticator , which will generate a numerical code (our second factor) that will change from time to time and is configurable. That is to say, the code that allows us the login at this moment, will change in, for example 30 seconds making it unusable. If someone gets hold of this code, he/she will no longer be able to use it even if he/she knows it.
From the part of the operating system that we want to protect, we need to use the libraries PAM , Pluggable Authentication Modules , that will complement the mechanisms of authentication by default, and in our case they will allow us to demand this second factor of protection.
2FA para SSH en Linux
Instalación de dependencias
In this case, Linux-PAM is the library we will use.
apt install libpam-google-authenticator
Configuración para el usuario
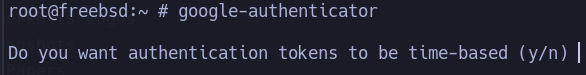
google-authenticator
This command starts the second factor configuration for the logged in user.
And we answer the questions that are presented to us and that serve to establish the behavior of the authenticator.
##### Do you want authentication tokens to be time-based (y/n)
PAM allows you to choose either sequence-based or time-based codes. The second option causes the entire code to change every so often. Authenticator apps are designed for this second option.
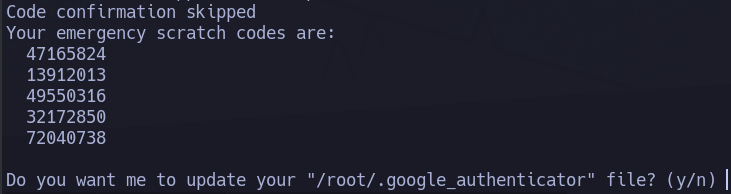
We will be presented with the QR code that we will have to scan with the app , to obtain the OTPs creation account that we will be using. We will also be given the alphanumeric option in case we have a problem with the mobile camera.

##### Enter code from app (-1 to skip):
##### Do you want me to update your "/root/.google_authenticator" file? (y/n)
Esto va a guardar las opciones de configuración del usuario para el segundo factor. Ni que decir tiene que es fundamental hacerlo.
##### Do you want to disallow multiple uses of the same authentication token? This restricts you to one login about every 30s, but it increases your chances to notice or even prevent man-in-the-middle attacks (y/n)
Es una protección contra ataques de repetición. El código que se utilice una vez, ya no podrá reusarse por nadie más.
##### By default, a new token is generated every 30 seconds by the mobile app. In order to compensate for possible time-skew between the client and the server, we allow an extra token before and after the current time. This allows for a time skew of up to 30 seconds between authentication server and client. If you experience problems with poor time synchronization, you can increase the window from its default size of 3 permitted codes (one previous code, the current code, the next code) to 17 permitted codes (the 8 previous codes, the current code, and the 8 next codes). This will permit for a time skew of up to 4 minutes between client and server. Do you want to do so? (y/n)
Aquí por seguridad se recomienda responder que **no** , ya que limitará a 8 códigos válidos cada 4 minutos.
##### If the computer that you are logging into isn't hardened against brute-force login attempts, you can enable rate-limiting for the authentication module. By default, this limits attackers to no more than 3 login attempts every 30s. Do you want to enable rate-limiting? (y/n)
If no further protection against brute force is available, it is recommended that you answer yes.
SSH configuration
For the service, we have to establish as a requirement the use of this module, so that we are asked for the OTP provided by the application, and reject logins that are not completed with it.
We will add the following line in the auth section of the /etc/pam.d/sshd file.
auth required pam_google_authenticator.so
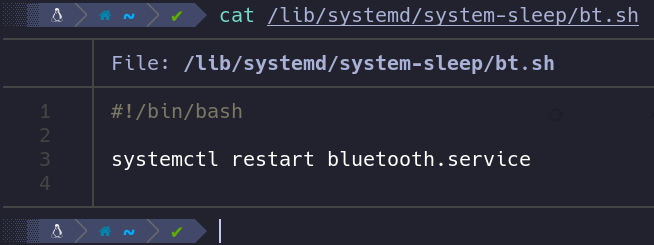
Service restart
2FA para SSH en FreeBSD
Install dependencies
For BSD , OpenPAM this is our library.
pkg install pam_google_authenticator
User configuration
This section is exactly the same as the one we have reviewed for Linux. We configure the second factor for the user.
google-authenticator



Config PAM in SSH
Likewise, we configure SSH authentication to set the second factor as mandatory. On the same file as in the Linux section, /etc/pam.d/sshd , same configuration line.
auth required pam_google_authenticator.so
Restart SSHD.
Google or Microsoft Authenticator configuration
This section is unique to any system in which we implement this control, and as it depends exclusively on the mobile device in which we install it, it will not be covered in this post.
Just emphasize that we will need to enter the code provided by the output of the google-authenticator command, or the reading of the QR code that it presents us (equivalent to the alphanumeric code).
Login using SSH with 2FA
If we have performed all these steps correctly, we should be prompted by the OTP after entering our user password.