Vulnerability management in FreeBSD
Like any other system, we need to keep those running FreeBSD up to date as well. Whether it is a physical machine, a virtual machine, or a jail. And up-to-date means not only integrating or installing new versions of the operating system itself or the packages and software installed on it. It also means keeping abreast of new vulnerabilities that impact both.
There are several ways to do this. One of them, which comes by default with the system, is to send an email to the root user on a daily and weekly basis with the result of the internal audit it performs on itself. An example of one of these mails is:
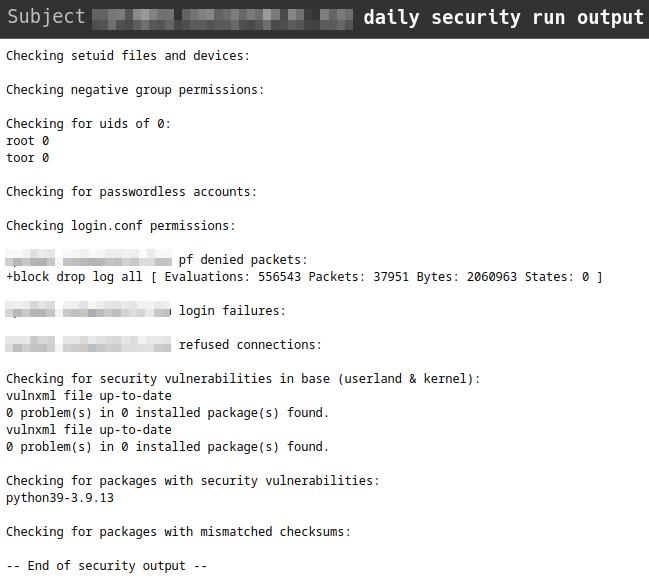
Which comes to summarize in this case that the vulnerable package is python-3.9.13.
To check what it is, we can log into the system and audit it manually:
doas pkg audit -F
And we will obtain in this particular case:
vulnxml file up-to-date
python39-3.9.13 is vulnerable:
Python -- multiple vulnerabilities
WWW: https://vuxml.FreeBSD.org/freebsd/d6d088c9-5064-11ed-bade-080027881239.html
Python -- multiple vulnerabilities
CVE: CVE-2020-10735
WWW: https://vuxml.FreeBSD.org/freebsd/80e057e7-2f0a-11ed-978f-fcaa147e860e.html
Python -- multiple vulnerabilities
WWW: https://vuxml.FreeBSD.org/freebsd/050eba46-7638-11ed-820d-080027d3a315.html
3 problem(s) in 1 installed package(s) found.
The possible vulnerabilities of the base system (the FreeBSD itself), do not appear in this report, for that there are other tools such as freebsd-version, freebsd-update.
As we can see, it provides references to consult exactly what these vulnerabilities consist of. From here the solution is simple:
doas pkg update
Which will result in:
Updating FreeBSD repository catalogue...
Fetching packagesite.pkg: 100% 6 MiB 6.6MB/s 00:01
Processing entries: 100%
FreeBSD repository update completed. 31741 packages processed.
All repositories are up to date.
Then upgrade the problematic packages:
doas pkg upgrade python39
With the output:
Updating FreeBSD repository catalogue...
FreeBSD repository is up to date.
All repositories are up to date.
New version of pkg detected; it needs to be installed first.
The following 1 package(s) will be affected (of 0 checked):
Installed packages to be UPGRADED:
pkg: 1.19.0 -> 1.19.1_1
Number of packages to be upgraded: 1
7 MiB to be downloaded.
Proceed with this action? [y/N]: y
[1/1] Fetching pkg-1.19.1_1.pkg: 100% 7 MiB 7.6MB/s 00:01
Checking integrity... done (0 conflicting)
[1/1] Upgrading pkg from 1.19.0 to 1.19.1_1...
[1/1] Extracting pkg-1.19.1_1: 100%
Updating FreeBSD repository catalogue...
FreeBSD repository is up to date.
All repositories are up to date.
The following 4 package(s) will be affected (of 0 checked):
Installed packages to be UPGRADED:
gettext-runtime: 0.21 -> 0.21.1
libffi: 3.4.2 -> 3.4.4
python39: 3.9.13 -> 3.9.16_2
readline: 8.1.2 -> 8.2.0
Number of packages to be upgraded: 4
18 MiB to be downloaded.
Proceed with this action? [y/N]: y
[1/4] Fetching python39-3.9.16_2.pkg: 100% 17 MiB 9.0MB/s 00:02
[2/4] Fetching libffi-3.4.4.pkg: 100% 36 KiB 36.5kB/s 00:01
[3/4] Fetching readline-8.2.0.pkg: 100% 343 KiB 350.9kB/s 00:01
[4/4] Fetching gettext-runtime-0.21.1.pkg: 100% 159 KiB 163.0kB/s 00:01
Checking integrity... done (0 conflicting)
[1/4] Upgrading libffi from 3.4.2 to 3.4.4...
[1/4] Extracting libffi-3.4.4: 100%
[2/4] Upgrading readline from 8.1.2 to 8.2.0...
[2/4] Extracting readline-8.2.0: 100%
[3/4] Upgrading gettext-runtime from 0.21 to 0.21.1...
[3/4] Extracting gettext-runtime-0.21.1: 100%
[4/4] Upgrading python39 from 3.9.13 to 3.9.16_2...
[4/4] Extracting python39-3.9.16_2: 100%
This would solve this problem.
This entry is not a guide on how to perform vulnerability management in personal or enterprise systems. It is simply a guide to testing and remediation. The collections of good practices in this sense must continue to be applied.